Connecting to a VPN hides your IP address – or at least that’s how it should work. But did you know there’s a browser feature that can leak your IP address while you’re protected by a VPN? What’s worse, that feature is default to most browsers.
We’re talking about WebRTC, and in this guide, we’ll tell you all about it. We’ll discuss what WebRTC is and what it does, how WebRTC leaks happen, and most importantly, how you can stay safe.
WebRTC Leaks
To put it simply, a WebRTC leak can reveal your public IP address to an attacker. Your public IP address is your address on the internet – think of it as your device’s phone number or home address. It’s how the internet knows where to send data so you can download files, view webpages, communicate with others, and so on.
WebRTC revealing your IP address isn’t problematic on its own. Your device shares its IP address constantly for normal internet activities like browsing websites. However, it becomes a critical security issue when you’re using a VPN specifically to mask that information.
One of the main reasons our experts recommend using a VPN is to hide your real IP address. It gives you a private IP address so you can do things like change your Netflix region and keep yourself anonymous while visiting a website. However, if WebRTC is leaking your IP address, it might be possible for others to still see your real IP address.
The result? Well, there are many things others can do with your IP address. For example:
- Your internet service provider can track your online activity.
- Governments can spy on you.
- Cybercriminals can access or steal personal data.
- Advertisers can send you personalized spam.
Know the Difference: Two or more devices can have the same private (local) IP address, but public (real) IP addresses are unique. That’s why concealing your public IP address is key to achieving online privacy.
What Is WebRTC?
WebRTC poses genuine security risks to VPN users, but it remains a vital technology for modern web communications. WebRTC stands for Web Real-Time Communication. It’s a free, open-source project that enables browsers and mobile apps to share audio, video, and data in real-time without plugins or downloads .1
The key advantage of WebRTC is peer-to-peer communication. Instead of routing through servers, devices connect directly to each other. This direct connection means faster video calls, smoother screen sharing, and quicker file transfers. A few of the major platforms that rely on this direct communication include:
- Google Meet and Google Hangouts
- Facebook Messenger
- Discord
- Amazon Chime
- Microsoft Teams
- Zoom (in browser mode)
- WhatsApp Web
The Problem With WebRTC
WebRTC is incredibly useful, but it creates a vulnerability if you’re trying to hide your IP address. When two devices establish a WebRTC connection, they must exchange their real IP addresses to communicate directly. Malicious websites or scripts can exploit this process and request your IP address through WebRTC, even when you’re connected to a VPN. The browser happily provides this information because it’s following WebRTC’s normal operating procedures.
To make matters worse, this IP exchange is fundamental to how WebRTC works – it’s not a bug, it’s a feature. You can’t simply tell WebRTC to skip this step. So how can we protect ourselves from WebRTC leaks? There are two options:
- Find and block WebRTC leaks
- Disable WebRTC on your browser entirely
The good news? Not everyone using WebRTC is automatically vulnerable. Quality VPNs have adapted their services to handle WebRTC traffic properly. In our testing of dozens of VPN services, we found that most reputable providers successfully prevent WebRTC leaks. Still, it pays to be vigilant, especially with your privacy on the line. So here’s how you can check for a WebRTC leak and prevent it from happening to you in the future.
Note: Firefox, Google Chrome, Opera, and Microsoft Edge are most vulnerable to WebRTC leaks because these browsers default to WebRTC.
How to Check for WebRTC Leaks
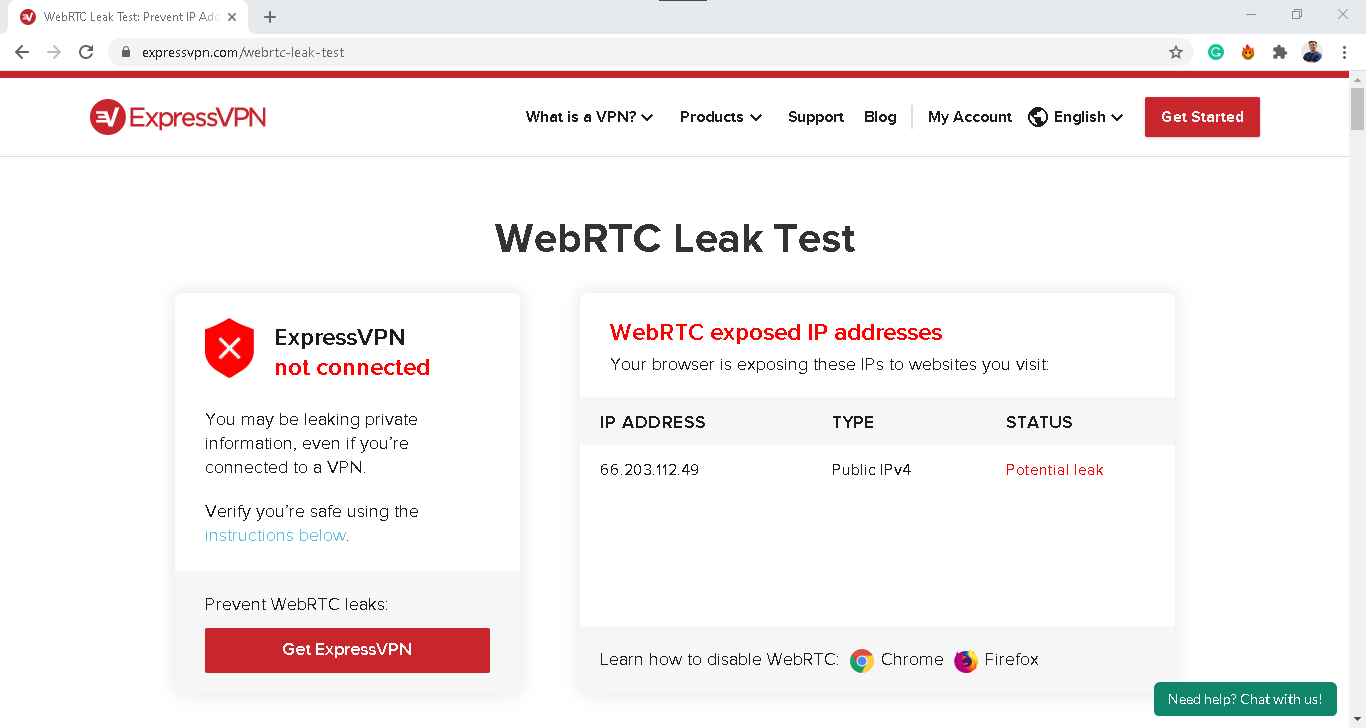
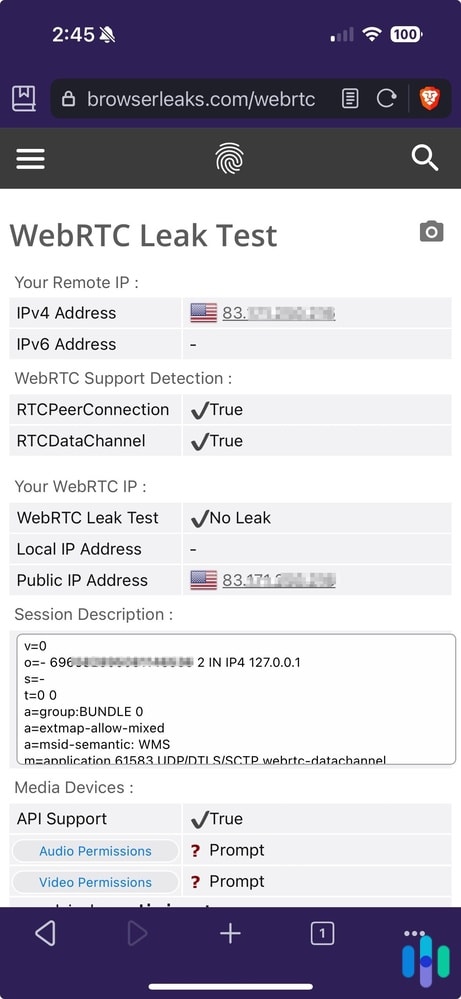
Testing your browser for WebRTC leaks takes just a few minutes. Here’s the process:
- First, find out and write down your device’s public IP address. If you need instructions on finding your IP address, check out these how-to guides:
- Next, use a WebRTC leak test tool. Several reliable options exist, including tools from BrowserLeaks or IPLeak.net.2
- If the IP address on the leak test tool matches your device’s IP address, then your browser might be leaking your IP address via WebRTC.
Remember that WebRTC is a browser feature, so if you use different browsers, be sure to test them all.
How to Block WebRTC Leaks
If you discover your browser is leaking your IP address through WebRTC, you need to take action immediately. The most effective solution is using a VPN that specifically addresses WebRTC vulnerabilities. While it’s true that some VPNs can’t handle WebRTC properly, the industry has largely adapted to this threat.
That’s why, when we’re testing VPNs, we always perform WebRTC leak tests on them. For example, all the best VPNs in our book passed the WebRTC leak test. These VPNs route all WebRTC traffic through their server’s address ensuring only your masked IP address is exposed. This lets you keep using WebRTC-dependent services while maintaining your privacy.
To check if your VPN is capable of blocking WebRTC leaks, here’s what you should do.
How to Block WebRTC Leaks with a VPN
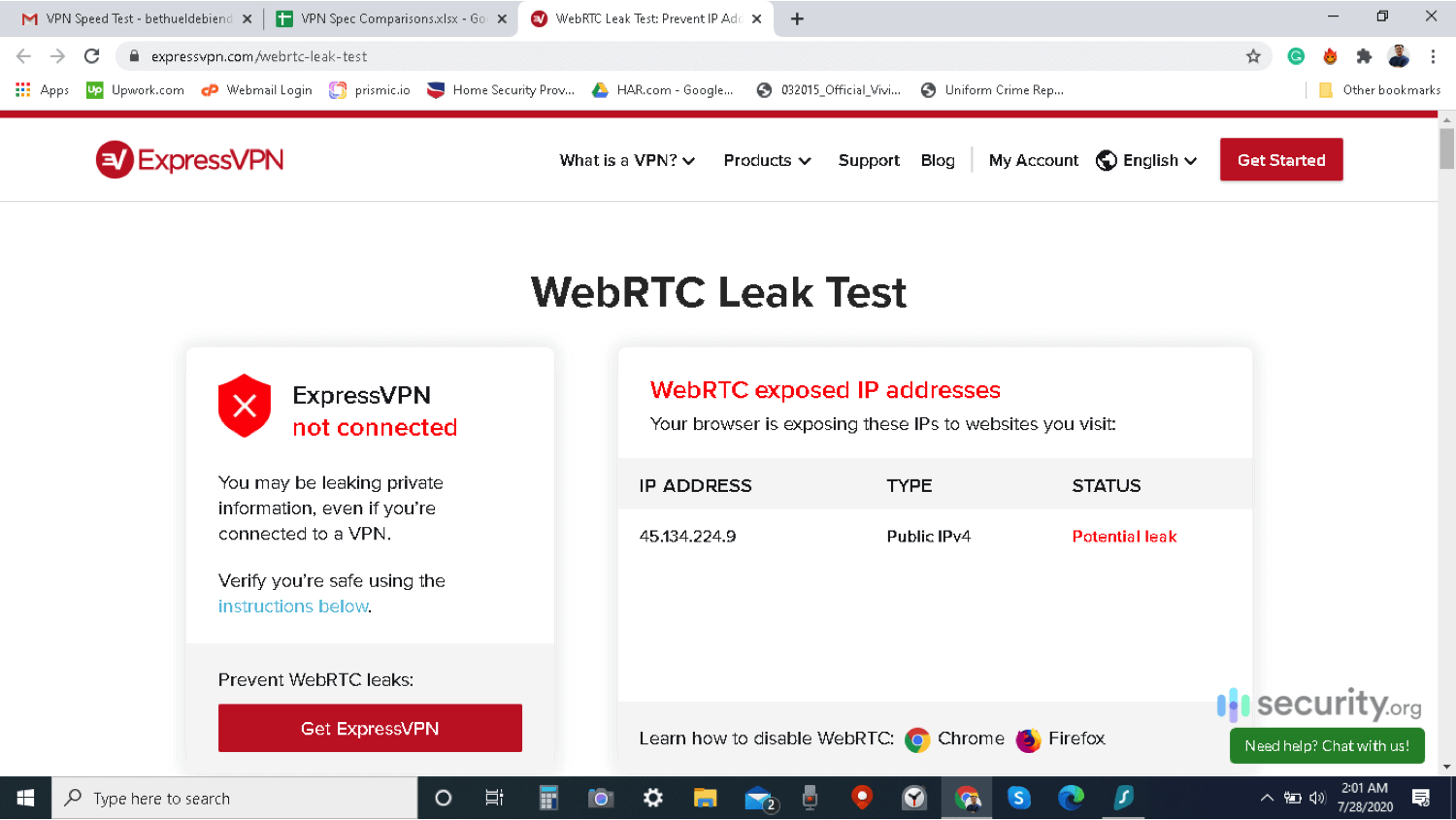
- Disable your VPN.
- Find and note your device's public IP address.
- Turn your VPN back on.
- Open your browser to any WebRTC leak test tool.
- If it's showing your device's real IP address from step two, then there is a leak. If it's showing a different IP address, then your VPN works.
If you find out that your VPN isn’t doing anything to prevent WebRTC leaks, you can contact your VPN provider and cancel your VPN service, switch to a new VPN, or proceed to the most surefire solution for WebRTC leaks: disabling WebRTC altogether.
Pro Tip: WebRTC leaks are one of the things we check when testing VPNs. Learn more about how we choose VPNs in our VPN guide.
How to Disable WebRTC
Think carefully before disabling WebRTC entirely. You’ll lose access to browser-based video calling, screen sharing, and many collaboration tools. If possible, we recommend using a VPN that blocks WebRTC leaks instead to preserve functionality while protecting your privacy. In case that’s not possible, though, disabling WebRTC altogether is also a solution – a surefire one. The catch is you won’t be able to use services that require WebRTC.
Here’s how you can disable WebRTC on Chrome, Firefox, and Edge. And keep in mind, you have to disable WebRTC on all the browsers you use on a regular basis.
Chrome
Google helped create and actively maintains WebRTC, so Chrome doesn’t offer a built-in way to disable it completely. That’s by design – Google wants WebRTC available for services like Google Meet. However, browser extensions can help you manage or block WebRTC functionality:
- WebRTC Network Limiter: This Google-made add-on restricts WebRTC to only using your default network path.3 It prevents WebRTC from discovering all your network interfaces, reducing (but not eliminating) leak risks. This works similarly to the best VPNs for Chrome, but instead of encrypted tunnels, the WebRTC Network Limiter uses proxy servers.
- WebRTC Control: This simple browser extension lets you turn WebRTC on and off. When WebRTC Control is on, your Chrome browser will stop using WebRTC.
- WebRTC Leak Prevent: Similar to the WebRTC Network Limiter, this extension prevents WebRTC leaks by controlling hidden WebRTC privacy settings and routing options.
- WebRTC Protect – Protect IP Leak: By default, this browser extension disables WebRTC. However, you can configure it to let you keep using WebRTC. If you do, it will control your WebRTC routing options, kind of like WebRTC Network Limiter.
Firefox
Mozilla actively develops WebRTC features, but unlike Chrome, Firefox provides a built-in option to disable it completely. If VPNs for Firefox can’t prevent WebRTC leaks, you can turn off WebRTC entirely by following these steps:
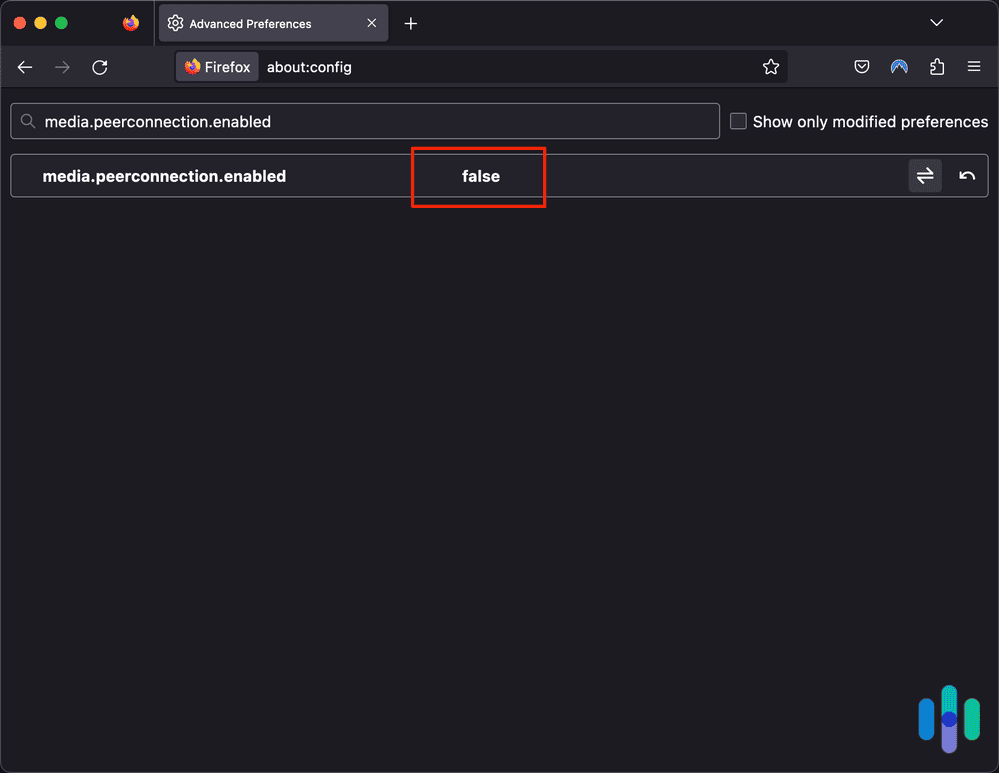
- Open Firefox.
- Type about:config into the address bar.
- Click “Accept the Risk and Continue” (the warning message may vary by Firefox version).
- Type media.peerconnection.enabled into the search bar.
- Double-click the result to change the value from True to False.
Edge
Microsoft Edge handles WebRTC similarly to Chrome, but it can be disabled as follows:
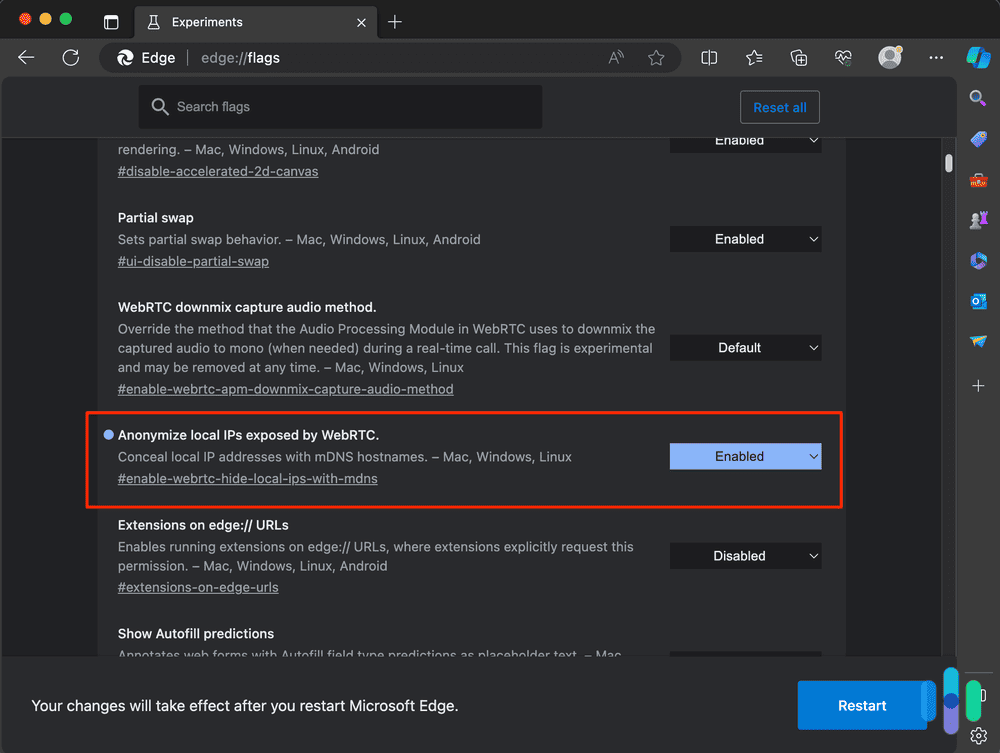
- Open Edge.
- Type edge://flags into the address bar.
- Hit Enter.
- Look for “Anonymize local IPs exposed by WebRTC” or search for “WebRTC” in the search box.
- Click the drop-down menu next to it and select Enable.
- Edge will prompt you to restart the browser for the new settings to take effect.
- Close and then reopen Edge.
What About Device IDs?
Beyond IP addresses, WebRTC can expose information about your device’s hardware. When a website requests WebRTC access, it can potentially see a list of your media devices – webcams, microphones, speakers, and other audio/video equipment. This creates a device fingerprint that could be used for tracking.
Modern browsers have implemented protections here. They no longer expose actual device IDs (those unique 16-digit hardware identifiers). Instead, browsers generate temporary hashes – scrambled versions of the device IDs that change when you clear your browsing data. However, until you clear that data, websites could use these hashes to recognize your device across sessions.
The privacy implications are real. Advertisers and data brokers increasingly use device fingerprinting for tracking when cookies aren’t available. Your unique combination of media devices, along with other browser characteristics, can create a trackable profile. The good news is, blocking WebRTC leaks, either by using VPNs or disabling WebRTC, prevents these pieces of information from leaking.
Recap
WebRTC powers many of the web’s most useful features – from video calls to file sharing – but its design creates legitimate privacy concerns. The technology’s need to establish direct connections between devices can expose your real IP address, even when using a VPN. As privacy becomes increasingly important in our digital lives, understanding and addressing WebRTC leaks is essential. Until browsers implement better privacy controls by default, your best protection comes from using a reliable VPN that handles WebRTC properly, or selectively disabling the feature when you don’t need it.
FAQs
To sum everything up, let's answer some FAQs about WebRTC and WebRTC leaks.
-
How do I fix WebRTC leaks?
You can fix WebRTC leaks by either using a VPN that blocks WebRTC leaks or disabling WebRTC on your browsers entirely. The former is the best solution if you want to enjoy all the functionalities that come with WebRTC, but with better security. VPNs that block WebRTC leaks allow WebRTC to work on your browser, but only through encrypted tunnels. That prevents anyone from stealing your IP address by exploiting WebRTC communications.
-
How do I stop WebRTC from leaking in Chrome?
To stop WebRTC from leaking in Chrome, you can use a VPN whenever you use Chrome. VPNs route WebRTC communications through encrypted tunnels, preventing WebRTC leaks. You can also use Chrome extensions like WebRTC Network Limiter, which reconfigures the routing options of WebRTC to make them more secure, or WebRTC Control to turn WebRTC on and off at will.
-
Should I turn off WebRTC?
Only disable WebRTC if you don’t use browser-based video calling or collaboration tools. If you regularly use these services, keep WebRTC enabled but use a VPN that prevents leaks. If you rarely use these services, disabling WebRTC provides the strongest protection against IP leaks.
-
How do I know if WebRTC is leaking?
You can find out if WebRTC is leaking by following these simple steps:
- Find and note your device’s public IP address.
- Visit a WebRTC leak test website like BrowserLeaks.
- If your public IP address matches the IP address on the website, then your WebRTC is leaking.
-
Can WebRTC leaks happen on mobile devices?
Yes, WebRTC leaks can occur on mobile browsers just like desktop ones. Mobile versions of Chrome, Firefox, Edge, and Safari all support WebRTC. Most mobile VPN apps protect against WebRTC leaks, but it’s worth testing your mobile browser separately, especially if you frequently use web-based video calling on your phone.